|
|
|
Read Me for BOFH's NetBarrier and ipfw Configuration Files.
Disclaimer!!!This file is provided as-is. I do not guarantee that this file will work correctly on your Mac,
nor do I take any responsibility for loss of connectivity or any other
problems that may result from using this file. Furthermore, I make no
promises that implementing this file will offer full and complete
protection from determined hackers, LAN sniffers, trojans or any other
attacks. I don't know (and I frankly don't care) for what purpose you are
going to use this file. The pre-configured NetBarrier file may work on earlier versions
of Mac OS X and/or NetBarrier - I haven't tried, and have no idea if it
will or how to go about importing it. Legally, this file is released under the GNU Public License (included in this download) which means you can edit, copy and redistribute it any way you like, as long as you publish it for free and in the public domain. As for credits, you can include them if you wish.
Software RequirementsMac OS X 10.2 or later. An important point to keep in mind when running NetBarrier (or any
other Firewall Software) is, not to run more than one firewall at the
same time.
Tech SupportIf you experience difficulties, I can provide some degree of Tech
Support, but before contacting me, make sure that you have read and
followed all the instructions provided here.
Other Recommended Security SoftwareOf course, a well regulated Firewall will go a long way to protect
you, but evidently it is not enough.
What's In There?The set-up is an original export from my own Mac, using an Airport Base Station as interface to the outside world. The setup should not be essentially different from any other router-based network. Otherwise, it contains the latest update (as of 06 December 2006) to the PeerGuardian list of blocked IP addresses. The pgupdate.sh file is a Shell Script, designed to download the latest version of the blocklist files from http://www.blocklist.org/ and convert it to a new NetBarrier Config-file.
Installing, Running and Uninstalling the ScriptsTo install the scripts with all the necessary binaries included, log in as administrator and doubleclick the Install.command file in the NBConfig disk image. Enter your password when prompted, and let the installation run its course. To uninstall everything, doubleclick the Uninstall.command file. Important Note: The installation will only work if run from the disk image. Do not copy the files to your hard disk and try to run it from there - it won't work! To run the update script manually, open a Terminal window
and type:
Using the pre-configured config-fileImportant!!! You may want to write down any special rules, as you will
need to re-enter them after the import. Sorry, but I haven't been able
to figure a work-around for that. Then select "File > Import Settings" and select the
Config-file.netb.
What Do The Rules Do?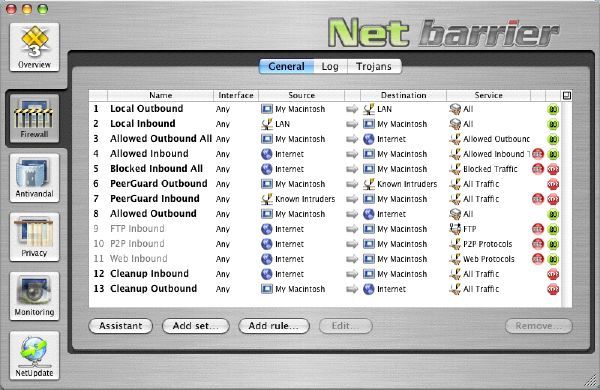
Rules 1+2: Allow any traffic to and from the
internal network (LAN) Rule 3: Allow outbound traffic on certain ports, such as http, https, pop3, imap, ssh etc. This means that you can still view the BSA or RIAA homepages, even though these organisations are blocked later on. Rule 4: Allow inbound traffic on ports needed to
run specific services, such as Network Time Synchronisation. Rule 5: Block inbound traffic on certain ports, not initiated from within, such as ping, snmp and other ports used to establish whether you are "available" for attacks. Rules 6+7: Block any traffic to and from the PeerGuard list of blacklisted IP addresses, not specifically allowed in previous rules. Rule 8: Allow any outbound traffic not specifically blocked in previous rules. Rules 9-11: Rules to allow inbound traffic when
running an FTP Server, Web Server, or running eDonkey, MUTE and
BitTorrent. Enable/Disable as needed. In rule 10, the UDP port 5044 and
TCP port 22080 are remnants of my personal setup, running on Overnet
and FreeNet respectively. Rules 12+13: The Cleanup Rules. Clean up after all
other rules, blocking any inbound and outbound traffic whatsoever. We
are working under the old East German rules here: Anything not
specifically allowed, is verboten! The files can be downloaded here: NBConfig.tar.gz BTW: I also have a shellscript for updating Apple's own ipfw. Get it here: ipfwpg.tar.gz
|